Learn how internet connections work to understand VPN better!
Virtual Private Networks or VPNs are amazing tools that can help mask IP addresses, increase our privacy and secure our connections. But many people don’t understand the nature of internet connections or networking, in general. And that makes explaining VPNs even harder.
So, this article will take a look at the TCP/IP model for networking. You can check out our OSI layer companion piece here .
Learning the 4 Layers
The TCP/IP model breaks up network connectivity into four distinct layers. Understanding how it all fits together is key to understanding how VPNs secure and anonymize our connections.
| Layer | Explanation |
|---|---|
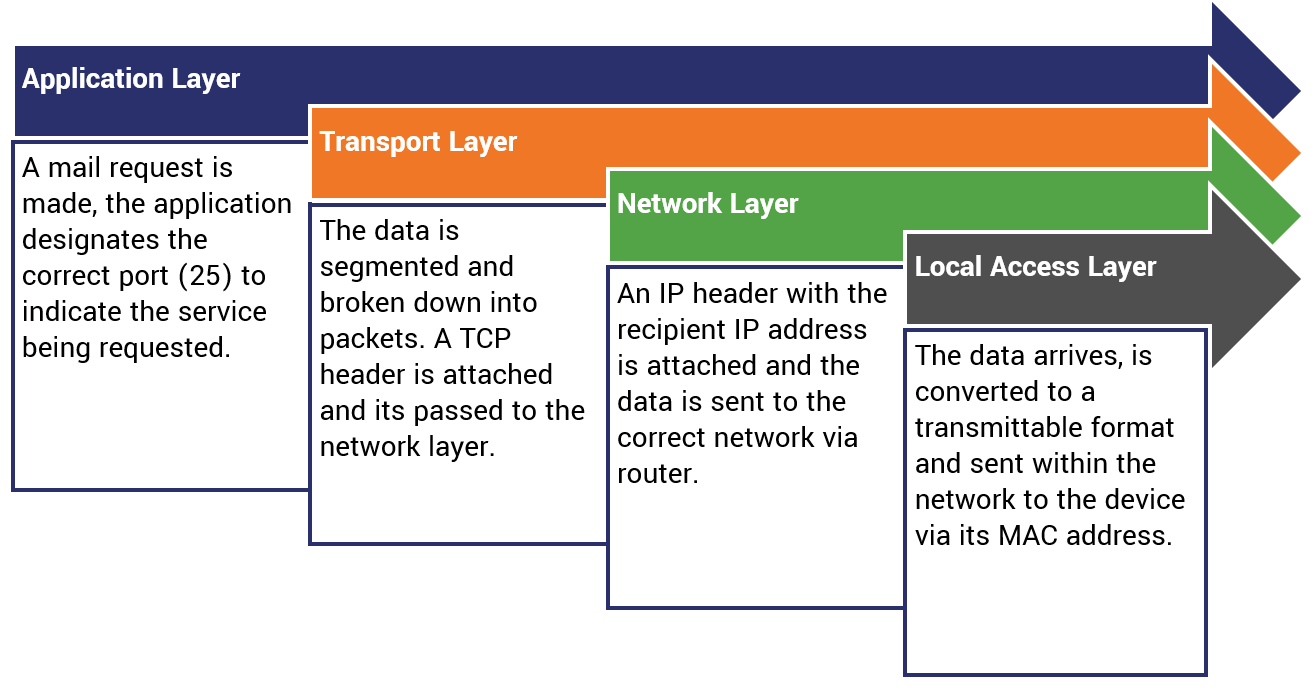
| Application | The application layer is what the vast majority of internet users interact with. This is the level where programs run and the web’s most common protocols (like SSL/TLS and FTP) occur. This is the layer where user requests are first initiated. |
| Transport | This layer handles end-to-end communication between devices on a network(s), the method for the connection (TCP or UDP) is decided on this level and the data being transmitted is segmented into packets and sent along to the network layer. |
| Network | The network layer handles network to network communication. IP address to IP address via router. This is the layer on which the Internet Protocol itself works. An IP header is affixed and the data is routed to the correct address. |
| Local Access | The local level handles the actual physical transfer of the data inside the network itself. It handles things like device MAC addresses and converting the data into a transmittable format like electromagnetic waves or electric signals. |
How does an Internet Connection Work?
Let’s look at an example of how an internet connection functions from the initial request at the application layer all the way down to the local access layer.
What TCP/IP layer does a VPN work on?
The beauty of VPNs are that they can be deployed on three of the four levels of the TCP/IP model:
- Application
- Network
- Local Access
The one thing to consider when deciding where to deploy your VPN, at what level, is that the security benefits only go up the stack – never down. Deploying a VPN on the network level will also secure the data at the Transport and Application layers. But deploying an application-level VPN, like an SSL/TLS VPN, doesn’t offer security down the stack so data at the transport and network levels may not be private.
Different VPN Protocols Deploy at Different Layers
The type of VPN you pick has a major bearing on the layer you can deploy it on. Not all VPN protocols are created equal. In fact, quite on purpose they have been created different to serve different functions at different layers of the stack.
| Protocol | Deployment Layer |
|---|---|
| IPSec | Network |
| L2TP | Network |
| OpenVPN | Application |
| PPTP | Local Access |
| SSL/TLS | Application |