How do businesses use a VPN?
A Virtual private network defends your business and the sensitive information it holds against malicious hackers or snoopers that are trying to compromise your security and privacy. It creates a secure tunnel and encrypts the flow of data between your organization and employees, thereby establishing secure communication.
The contemporary trend of allowing employees to work remotely is widely prevalent among many businesses. In this regard, a VPN allows your employees to safely access your organization’s network even on a vulnerable public Wi-Fi hotspot connection.
A VPN also helps you to carry out anonymous market research without revealing your company’s identity, as it spoofs your details like IP address and location. If you are a frequent traveler, you might need a VPN connection to experience the internet without any censorship.
While a VPN offers competitive advantages to your business, let’s not forget to look at the risks arising from it and ways to tackle them.
Understanding a VPN connection and malware attacks
Does a VPN protect you from malware?
Unfortunately, No. A VPN does not protect you against malware attacks. It just creates a secure pathway to reach your internet destination without any third-party interception. While some premium VPN providers come with features that block malicious advertisements and malware, most of them do not assure guaranteed protection against malware attacks.

Hence your organization is required to have licensed antivirus software along with a VPN connection, which protects your internal network from unpleasant interceptions. You should also understand the fact that most of the free VPN providers are easy targets for malware attackers. So, get a professional VPN provider today to experience absolute business security.
Quick Tip: Your employees are also required to exercise caution that prevents them from clicking on malicious links even when connected to a Virtual Private Network.
Credential-based Attacks:

Positively, your business can mitigate the risk of credential-based attacks by choosing a VPN connection with robust and multiple authentication protocols. Let’s us not forget the role of multi-factor authentication that securely verifies user identity.
You can read about the different types of VPN protocols to understand VPN connection and authentication better.
VPN’s Split Tunneling can be susceptible to online attacks
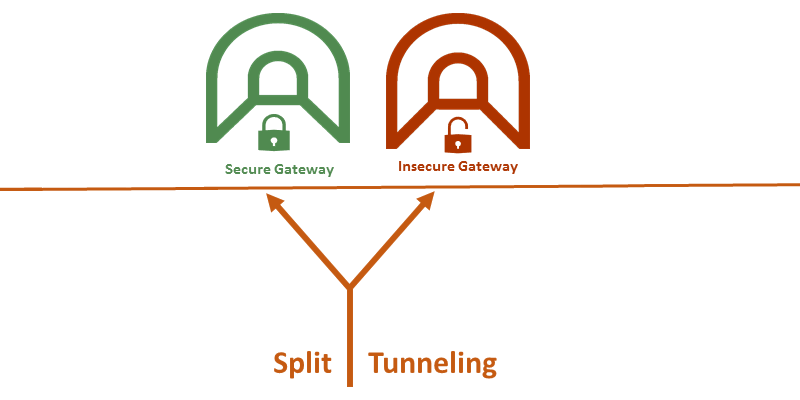
As a result, snoopers can bypass any firewall protection and access your organization’s network directly through the unprotected public network. Hence a VPN connection that has enabled split tunneling might be vulnerable to cyber-attacks that include hacking and malware infection.
Resolution: When a user connected to a VPN chooses to leave the default remote network gateway, the Internet Connection Sharing (ICS) feature gets auto enabled. This feature allows a VPN client machine to access public networks through a NAT router. Network administrators can mitigate the risk of split tunneling by creating a group policy to disable this ICS feature on devices that are authorized to connect to the internal network using a VPN client. Or you can directly disable the split tunneling feature itself. Installing host-based firewalls is also an effective way to tackle the threats arising from split tunneling.
Bottom Line:
- Organizations should understand the significance of educating their employees on security awareness and start conducting frequent awareness sessions.
- Organizations can use host identity verification to authenticate remote users’ identity. Your company can validate the specified end device parameters of the client including digital certificates, registry entries, distinctive files and more.
- Create rigorous security standards and policies to shield your organization’s internal network while granting access to remote users.
- Go for a business VPN service provider. A free VPN can never overcome your organizations’ privacy and security challenges completely. Free VPNs can be frustrating because of slower speeds, bandwidth limits, connection drop and increased traffic. Most of all, Free VPNs are after your sensitive data. They sell it to targeted advertisers, which might even reach the hands of notorious hackers. Get a premium VPN and appreciate the value it offers.
Important Resources to Read
- Top 7 Ways to Enhance the Security of Your Home Wi-Fi Network
- 7 Tips to Keep Your Child Safe Online From Bullies & Other Security Threats
- Take Your Mac Security to the Next Level With These Tools
- Top 10 Tips for Mobile Phone Security
- Benefits Using VPN for Business
- 7 Tools to Stay Completely Anonymous Online
- Should You Use a VPN at Home or Not?